Hybrid work is fundamentally changing the cybersecurity landscape, creating new threats outside the familiar office. The problem of unprotected home networks and public Wi-Fi vulnerabilities requires the implementation of modern, adaptive defense measures. This article provides practical recommendations for strengthening security to help IT professionals, executives, and anyone looking to protect corporate data in the new environment.
Challenges of Hybrid Work Security
Challenges of Hybrid Work Security Hybrid work environments fundamentally reshape the security landscape that organizations must navigate. In contrast to traditional on-site setups — where IT teams maintain a well-defined company network with robust enterprise-grade protections — hybrid work extends security boundaries into employees’ homes, public spaces, and other remote locations. This distributed model introduces new security risks that were less prevalent in conventional office settings.
For example, when employees access corporate resources via home networks or public Wi-Fi, the level of network security often falls short of what a centralized office offers. Home networks might lack advanced firewalls, regular security audits, and intrusion detection systems, while public networks can be easily targeted by malicious actors.
📝 ResearchGate emphasizes that remote working requires strategies specifically designed for distributed environments. It is important to take layered security seriously and to perform continuous monitoring to mitigate vulnerabilities inherent in hybrid workspaces.
Traditional VS Hybrid Work Security Models
| Aspect | Traditional On-Site | Hybrid Work |
| Network Boundary | Well-defined, controlled company network | Distributed across home, public, and mobile setups |
| Security Measures | Enterprise-grade firewalls, regular audits | Varies by location; often lacks uniform protection |
| Risk Exposure | Lower risk due to controlled environment | Increased vulnerability to security risks |
Key Security Risks in Hybrid Work
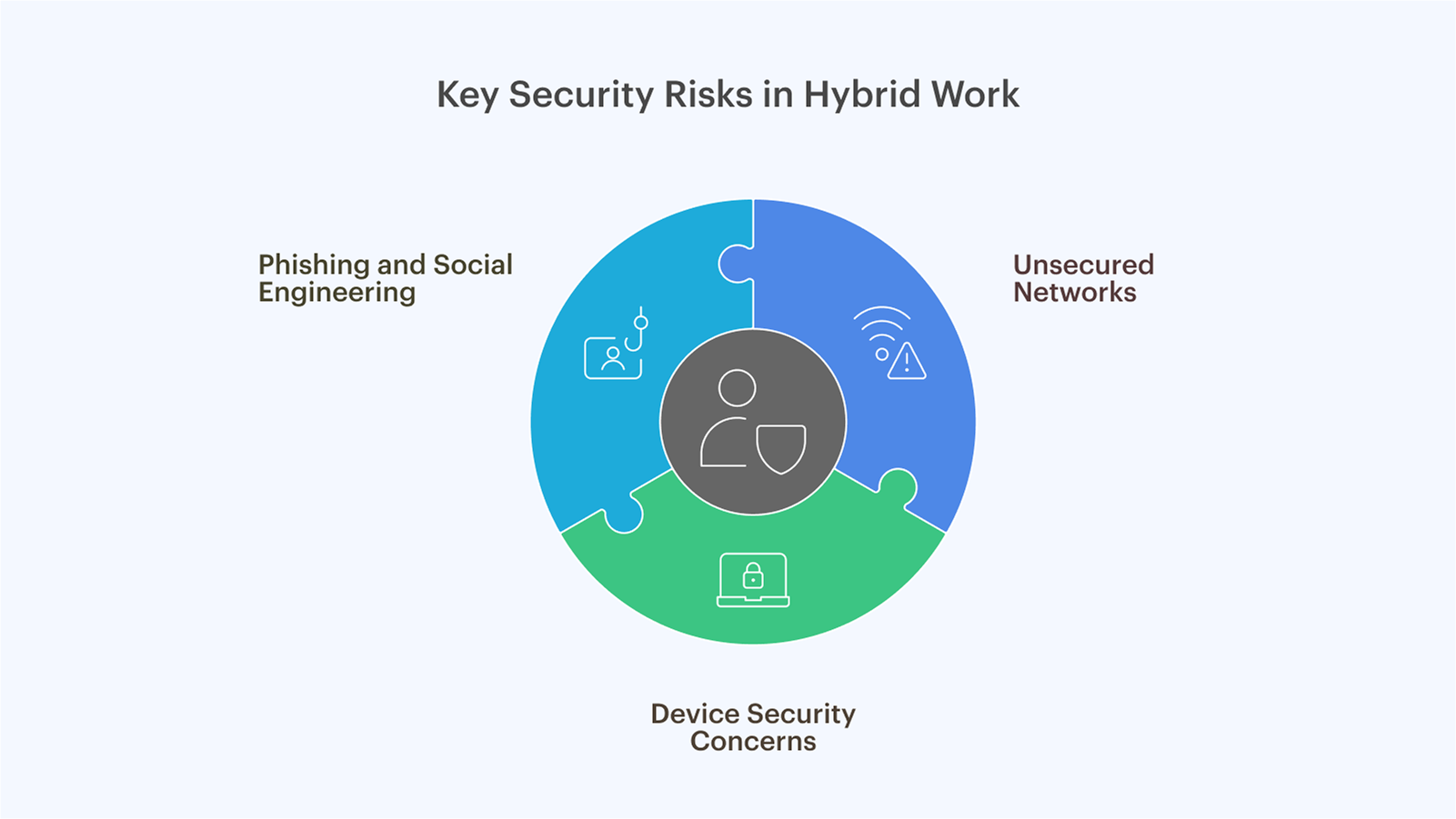
The transition to hybrid work brings several critical vulnerabilities that require immediate attention. Some of the key risks include:
- Unsecured Networks: Employees using home Wi-Fi or public hotspots may bypass traditional security perimeters. For instance, a marketing executive connecting to sensitive customer data via an unsecured café Wi-Fi could inadvertently expose proprietary information.
- Device Security Concerns: Devices used outside the office are more susceptible to loss, theft, or compromise. Without proper mobile device management, a laptop left unattended in a public space could lead to severe data breaches if it contains unencrypted corporate information.
- Phishing and Social Engineering: Remote workers often face a higher risk of phishing attacks and other malicious exploits, as they lack immediate support from on-site IT teams. This increased exposure makes it easier for cybercriminals to execute phishing attacks.
Security Best Practices for Hybrid Work
A practical security framework for hybrid work involves both technological solutions and employee training. Below is a summary of key practices:
- Establish clear security policies: Define protocols for remote work and set expectations for secure access to company networks.
- Implement secure access solutions: Use advanced technologies such as SASE and cybersecurity zero trust models to verify every access request.
- Regular training: Conduct ongoing security awareness sessions to prepare employees for potential security breaches.
- Device management: Enforce policies that ensure all devices, whether personal or corporate, meet established security standards.
- Continuous monitoring: Use monitoring tools to identify and respond to threats promptly.
Implementing Zero Trust Security in Hybrid Work
🧠 The Zero Trust model has become the gold standard for hybrid work security. Operating under the principle of “never trust, always verify,” this approach eliminates the distinction between internal and external networks. Instead, every user, device, and access request is authenticated and authorized, regardless of the connection source.
Key steps to implement Zero Trust include:
- Data Mapping: Identify sensitive data and monitor its flow across networks.
- Strict Identity Verification: Apply multi-factor authentication (MFA) to ensure secure access.
- Minimal Permissions: Grant users only the access necessary to perform their roles.
- Continuous Monitoring: Log all network activities to detect anomalies.
- Micro-Perimeters: Establish small, secure zones around critical resources.
Cloud Security and Protecting Remote Workforces
💡 Cloud services have become the backbone of modern business operations, especially for a distributed workforce. Securing these environments involves a distinct set of measures compared to traditional on-premises systems. SASE (Secure Access Service Edge) has emerged as a key framework in this domain by combining networking and security functionalities.
Benefits of SASE include:
- Uniform Security Policies: Consistent protection regardless of user location.
- Simplified Management: Reduced complexity by replacing multiple point solutions.
- Enhanced Encryption: Strong encryption of sensitive data transmitted over various networks.
- Improved Performance: Secure access is optimized by directing traffic closer to the user.
- Greater Visibility: Better monitoring across the distributed environment.
The expanding data protection market, as reported by Fortune Business Insights, is a testament to the growing recognition of these challenges, with significant investments in cloud security and data protection tools driving innovation in the hybrid work era.
Employers' Role in Hybrid Work Security
Employers play a pivotal role in ensuring robust security measures for hybrid work environments. Rather than acting as obstacles, security policies should enable productivity while protecting company assets. Employers must develop clear policies and provide the necessary infrastructure and training for all employees.
Key responsibilities for employers include:
- Developing and enforcing security policies: Tailor guidelines to the hybrid work context.
- Resource allocation: Invest in security tools, training, and infrastructure.
- Consistent standards: Ensure that security measures are uniformly applied across all work settings.
- Monitoring and precaution: Use monitoring systems to preempt potential security breaches while respecting employee privacy.
- Fostering a security culture: Encourage every employee to take ownership of cybersecurity.
Essential Security Tools for Employers and IT Leaders
VPNs, Firewalls, and Endpoint Security
The backbone of hybrid work security relies on three critical technology pillars: VPNs, firewalls, and endpoint security. Each component plays a specific role in protecting the company network and devices.
- VPNs: Business-grade VPNs create encrypted tunnels for remote work, ensuring that data security is maintained even over unsecured public Wi-Fi. Features like split tunneling allow only critical business traffic to pass through corporate channels, optimizing network performance.
- Firewalls: Next-generation firewalls go beyond traditional port filtering. They incorporate application awareness, intrusion prevention, and advanced threat protection. Such systems enforce consistent security policies across diverse environments, reducing the risk of unauthorized access.
- Endpoint Security: Endpoint detection and response (EDR) platforms safeguard individual devices by monitoring for malware and suspicious activity. These tools continuously apply security patches and enforce compliance with corporate policies, which is crucial when devices operate outside of the office.
To further reinforce security in a hybrid work setup, UnSpot’s Internal Help Desk offers an effective solution. This tool ensures that employees receive prompt assistance with technical and security-related issues, whether they work remotely or in the office.
AI-Driven Security Solutions for Hybrid Work
Artificial intelligence has transformed cybersecurity by offering advanced threat detection and rapid response capabilities. AI-driven security tools continuously monitor network traffic and device behavior, detecting anomalies that manual systems might miss. This is particularly important in hybrid environments, where traditional security perimeters no longer exist.
Key advantages of AI-driven security solutions include:
- Behavior Analysis: AI systems learn user behavior patterns to detect account compromises early.
- Automated Responses: Threats are contained without waiting for manual intervention, reducing the window for data breaches.
- Continuous Learning: These systems evolve with emerging threats, improving detection accuracy over time.
- Reduced Alert Fatigue: Intelligent prioritization helps security teams focus on genuine risks instead of false positives.
- Enhanced Monitoring: Comprehensive visibility across all endpoints ensures sensitive data is monitored and secured.
🚀 A list of basic safety equipment: Business-grade VPN solutions with split tunneling capabilitiesNext-generation firewalls with advanced threat detectionCloud-based endpoint detection and response (EDR) platformsIdentity and access management systemsData loss prevention (DLP) toolsSecure email gateways with anti-phishing measuresMobile device management platformsCloud access security brokers (CASBs)
Legal and Compliance Considerations for Hybrid Work Security
The transition to remote work brings legal complexities that demand careful attention to data security and compliance. Organizations must implement clear security policies to ensure corporate and regulatory standards are met, regardless of work location. For example, a financial firm must secure client data whether an analyst is in the office or at home.
Key considerations include:
- Data Security: Protect sensitive information through robust encryption and secure transmission protocols.
- Regulatory Compliance: Align security policies with frameworks like GDPR and HIPAA.
- Corporate Governance: Adapt existing policies to cover remote work challenges.
Security Policies for Hybrid Workforces
Effective security governance in hybrid environments hinges on clear policies that balance employee flexibility with data protection. Central to this is a robust BYOD framework. Employees using personal devices must follow guidelines that reduce security risks without hindering productivity.
Key policy elements include:
- Device Registration: Approve and register all personal devices.
- Minimum Security Standards: Enforce encryption, antivirus, and regular updates.
- Application Controls: Define whitelists/blacklists for corporate apps.
- Remote Wipe: Enable wiping of sensitive data on lost or stolen devices.
✔️ Hybrid Work Security Best Practices Checklist
A systematic approach makes implementing robust security measures for hybrid work straightforward. Begin by:
- Conducting a comprehensive risk assessment
- Developing clear security policies for both remote and in-office work
- Implementing identity and access controls (with MFA)
- Deploying endpoint protection across all devices
- Establishing secure network access (VPN/ZTNA)
- Enabling cloud security controls and continuous monitoring
- Scheduling regular security awareness training
- Creating an incident response plan
Common Cybersecurity Mistakes to Avoid in Hybrid Work
Even the best cybersecurity measures can be undermined by basic oversights. In hybrid work, common mistakes include:
- Inadequate Authentication: Not enforcing multi-factor authentication (MFA) across all systems leaves accounts vulnerable.
- Poor Device Management: Lacking oversight of personal and corporate devices increases the risk of unpatched endpoints.
- Weak Network Segmentation: Failing to create secure zones enables lateral movement in case of a breach.
- Insufficient Training: Limited cybersecurity awareness makes employees more susceptible to phishing and malicious attacks.
Emerging Trends in Hybrid Work Cybersecurity
Cybersecurity in hybrid work is rapidly evolving as organizations implement advanced, adaptive security measures to mitigate emerging risks. Future trends include:
- Adaptive Security Architectures: Dynamically adjust controls based on user location, device health, and behavior.
- AI-Driven Security: Use behavioral analysis and anomaly detection to spot early signs of breaches.
- Consolidated Platforms and Automation: Simplify management and accelerate response times.
- Enhanced Monitoring: Extend visibility into both virtual and physical environments.
Frequently Asked Questions
What is a hybrid security control?
A hybrid security control is a system that protects company data in a hybrid workplace — where employees work both in an office and remotely. It combines policies and security measures with technology solutions like software, network and endpoint monitoring, and credential checks. This control adapts to the hybrid work model by securing all work devices, whether they are on-premise, at home, or even used in a coffee shop. The goal is to make security proactive and easier to manage across different environments.
Key elements include:
- Clear security policies that require employees to follow specific guidelines.
- Device management tools that secure laptops, smartphones, and bring your own device setups.
- Remote access solutions, similar to office 365, that protect data even outside traditional office space.
- Regular monitoring to stay aware of potential security threats.
How do you maintain security when employees work remotely?
Maintaining security when employees work remotely involves simple steps that protect data and reduce potential threats. You need to use secure technologies and set clear policies and security rules that all team members follow.
Here are the main practices:
- Secure Access: Use VPNs and remote access tools to ensure that data transmission is safe.
- Device Management: Ensure all work devices — whether company-issued or personal (as in bringing your own device) — have up-to-date antivirus and security software.
- Regular Training: Educate employees on safe practices, such as avoiding public Wi-Fi in places like a coffee shop without a secure connection.
- Enforce Policies: Require employees to follow best practices, such as using multi-factor authentication, to safeguard their credentials.
- Monitor Activity: Use tools to continuously check the security of your hybrid workplace, reducing risks on both the network and endpoint.
These steps help ensure that even in a flexible work setup, security remains strong and proactive.